cross-posted from: https://lemmy.world/post/1287053
Be alert, Please do not launch a new tab of Lemmy.World. Having tabs already open with this site is fine but as soon as you do you will be bombarded with awful content with malicious intent to cause shock, disgust and distress.
In the meantime use alternative instances, other instances are not affected by this compromise. Do not open any links/posts from the user MichelleG.
Thanks for reading, please stay safe out there Lemmy users!
Update: Lemmy World is under attack again.
Update: I am not a super code-literate person so bare with me on this… But. Still please becareful. There appears to be a vulnerability.
Users are posting images like the following:
And inside hidden is JavaScript code that when executed can take cookie information and send it to a URL address.
Among other things. At this time if you see an image please click the icon circled before clicking the link. If you see anything suspicious, please report it immediately. It is better a false report than a missed one.
looks like we survived the gay porn attack
Updating profile with “I survived 🍋 🎉 of July 2023”
The worst part was it wasn’t even good gay porn.
Liberal terrorism
We back in business now :)
It is concerning as I have received a message from a compromised admin 1 hour ago telling me that an app developer wanted me to help them with mod tools.
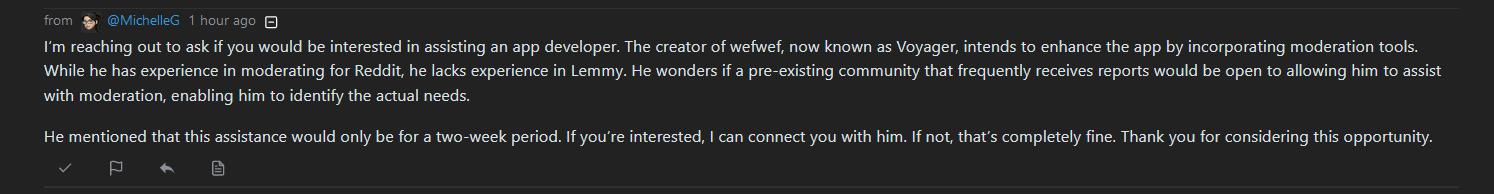
Hard to know if this is genuine or not, but given what has happened I am going with an attempt at breaching my account.
That, is actually kind of fascinating and may be important info for someone doing a follow-up investigation. If that was the bad actor phishing for moderation access, why would they need that, when they already had an admin account? If it was legit, then it’s super sus. whoever this app developer was needs to have a little light shone on them.
Could be where the DM from the admin was legitimate but got compromised following contact by this app developer.
It is also possible nothing of the sort happened. The timing was just extremely alarming
This is all part of growing pains on a new admin suddenly owning the top lemmy instance because they knew a little bit about branding.
As I’ve said before, I’m giving the admin a couple months and I feel they’ve done a fantastic job already.
Let this be a lesson to all. Use long passwords with a password manager to deter brute force attacks. Use 2FA for your account. It’s security 101.
The Lemmy 2fa has some compatibility issues and doesn’t verify you have working tokens
Still better than no 2fa at all. And these bugs will get fixed in the future, so why not use it now already?
Interesting. That does present a serious issue then.
I think this carrying on without providing more information is reckless. Does an actual admin from this instance really know what happened or are you just taking a bunch of random commentary and speculation as gospel then telling the users “we’re good.”
I am a moderator of this community, not an admin of Lemmy.World
I know about as much as you. The difference is I have been spending time researching and discussing findings with other mods rather than sleeping which is what I should be doing.
I found critical information that I thought important to share. That is all there is to it. If you do not feel safe using Lemmy.World you should login to another instance.
The owners of Lemmy.World are also in the EU so are likely still asleep or awake and trying to figure this shit out.
TBF, at least you’re doing something.
You do you. I would tell my users I have no idea what’s going on, and definitely not say “using your open tabs is probably fine.”
The attack involved a redirect that only affected pages that were freshly opened. If you had tabs that were opened before the attack no redirects happened, no malicious URLs of the sort. It showed the website as it was normal.
That statement was in fact true. The attack only happened when you opened a new tab of Lemmy.World
What happens if you refresh said tab?
deleted by creator
Going through an app also prevents the awful redirects.
Speaking of apps. Seems like this is a possible attack vector.
Maybe a malicious actor copies code of one of the popular apps (Voyager/wefwef), adds code to extract JWT token or whatever auth token, gathers list of high value targets (admins / mods of large instances or communities), then hijacks instance.
Very easily could have been much worse. On the flip side, glad it was just a script kiddie
Why the hell do people have to be complete assholes? I had just clicked a link and got all the crap, then couldn’t go to the homepage or any of the posts in my history. I thought I got a virus until I tried it on my other device.
Honestly should be just as illegal as vandalism.
I mean it kinda is, the hacker exposed potential children to p*rnographic content.
The home page seems to be operating normalish now
Update: Things seem to be calm about the moment. If there is any updates please inform me.
I’m checking on mobile web browser atm, everything seems fine.
Things are slowly getting restored, the mod that was compromised has been removed. Hopefully nothing more happens. I’ll unpin this post as soon as I am 100% sure on that though.
Thanks for helping take care of it, that was a pretty quick response from you guys. I’m betting the talk for the next day is gonna be all about 2FA. lol
Someone posted lemmy.world getting federated with threads. Was that legit?
It was the admin account mentioned in the post, MichelleG, which got compromised. No one is dumb enough to federate with that trash, it was just a troll.
was the hacker
lemmy.blahaj.zone just went under to it too
FYI: Y’all still only federated with threads.net :)
Aaw did I miss it? :(